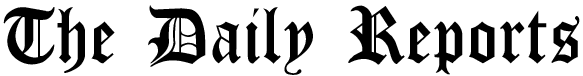Iran is running two reconnaissance tasks in the internet, focusing on in excess of 1,000 nonconformists, as indicated by a main digital protection organization.
The endeavors were coordinated against people in Iran and 12 different nations, including the UK and US, Check Point said.
It said the two gatherings included were utilizing new procedures to introduce spyware on targets’ PCs and cell phones.
Furthermore, this was then being utilized to take call accounts and media documents.
One of the gatherings, known as Domestic Kitten or APT-50, is blamed for fooling individuals into downloading pernicious programming on to cell phones by an assortment of means including:
Repackaging a current adaptation of a genuine computer game found on the Google Play store. Impersonating an application for an eatery in Tehran. Offering a phony versatile security application. Giving an undermined application that distributes articles from a neighborhood news office. Providing a contaminated backdrop application containing favorable to Islamic State symbolism. Taking on the appearance of an Android application store to download further programming. The American-Israeli organization’s analysts archived 1,200 casualties being focused by the mission, living in seven nations.
There had been in excess of 600 effective diseases, it said. The subsequent gathering, known as Infy or Prince Of Persia, is said to keep an eye on the home and work PCs of dissenters in 12 nations, extricating delicate information in the wake of fooling individuals into opening malignant email connections.The Iranian government has not remarked on the report.
Homegrown Kitten’s activity was first distinguished in 2018. Also, Check Point said there was proof it had run in any event 10 missions since 2017. Four of these were as yet dynamic, with the latest start in November 2020.
Also, it was utilizing an Iranian blog website, Telegram stations, and instant messages to draw individuals into introducing its contaminated programming, which the analysts have named Furball, which could:
- Record calls and different sounds
- Track the gadget’s area
- Gather gadget identifiers,
- Snatch instant messages and call logs
- Take media documents, including recordings and photographs,
- Acquire a rundown of other introduced applications
- Take records from outside capacity.
The 600 effective diseases are said to have included nonconformists, resistance powers and individuals having a place with the Kurdish ethnic minority in:
- Iran
- The US
- Britain
- Pakistan
- Afghanistan
- Turkey
- Uzbekistan
The other gathering, Infy, is said to have been working as far back as 2007.
Its latest action had focused on PCs, with counterfeit messages with alluring substance, ordinarily, with an appended archive, Check Point said.
One example provided was of a document apparently about loans being offered to disabled veterans.
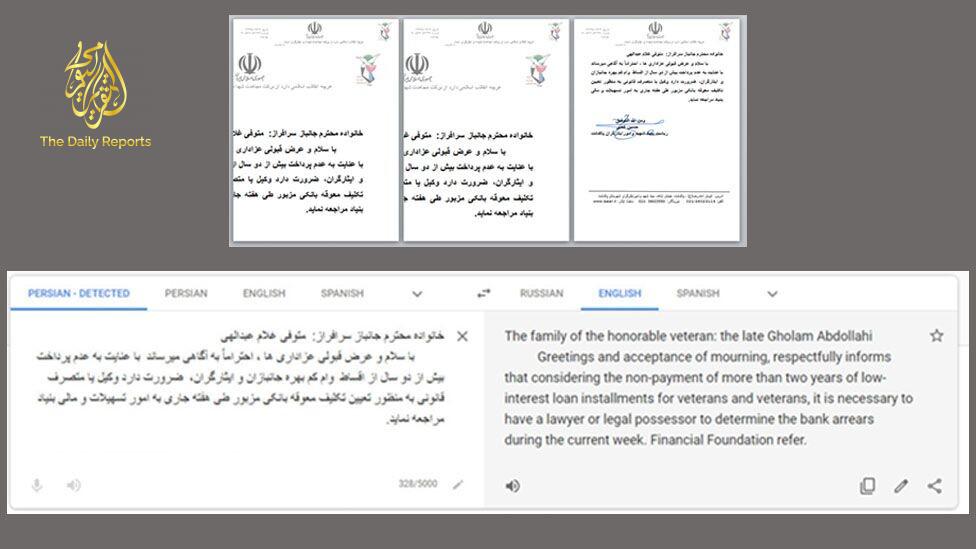
Two reports as of late utilized are said to have incorporated a photograph of an Iranian lead representative, with supposed contact subtleties.
The analysts said Infy’s capacities were “far prevalent” to most other realized Iranian missions, because of its capacity to be profoundly specific about its objectives and to have by and large have gone undetected.
“Obviously the Iranian government is putting critical assets into digital tasks,” Check Point digital examination head Yaniv Balmas said.
“The administrators of these Iranian digital reconnaissance crusades appear to be totally unaffected by any counter-exercises done by others, despite the fact that the two missions had been uncovered and even halted before.
“They have just restarted.”