The Hamas fear bunch again endeavored to keep an eye on the Israeli military by assuming responsibility for many fighters’ cellphones in the course of recent months, utilizing spyware they’d persuaded the administration individuals to download by acting like youthful Israeli ladies via web-based networking media, the Israel Defense Forces said Sunday.
The military said it defeated this digital assault in a joint exertion with the Shin Bet security administration, named Operation Rebound, throughout the end of the week, bringing down the servers Hamas utilized in its exertion.
The IDF said it didn’t trust Hamas had gotten any huge insight in its activity, yet would before long know all the more definitely as it would check the telephones of the considerable number of troops included. The IDF would not say exactly what number of fighters were influenced, however said it was in the “low hundreds” and that solitary the telephones of recruited warriors and low-positioning officials were tainted with Hamas’ spyware.
This was in any event the third endeavor by Hamas lately to “catfish” Israeli warriors — professing to be another person on the web so as to dupe the person in question — so as to introduce programming on their telephones that the fear gathering could use to accumulate insight on the IDF.
The leader of the IDF’s operational security division — who must be distinguished by her position and first Hebrew letter of her name, Col. “Resh” — said the military expected this would not be the last time that Hamas attempts this kind of digital activity, as there are a few individuals from the fear association explicitly entrusted with such endeavors, however she wouldn’t distinguish them by name.
Comparative endeavors were revealed and hindered by the military in January 2017 and July 2018. Hamas’ digital tasks division in Gaza City was besieged by the IDF in May 2019 during a two-day fight with the fear bunch in the Strip.
Resh said right now utilized increasingly advanced techniques and advances in its catfishing exertion. She said this most recent exertion by Hamas occurred a while back and that the military immediately got mindful of it, yet permitted it to proceed so as to more readily follow the system that was being utilized.
The fear gathering’s agents acted like new female foreigners with hearing or vision issues so as to both preemptively clarify away any syntactic or phonetic blunders and to keep the fighters from requesting to talk by telephone or video calls, Resh said.
The Hamas agents additionally made profiles for the invented ladies with names including Rebeca Abuksis, Eden Ben Ezra, Sarah Orlova, Noa Danon and others, over numerous web-based social networking stages — Facebook, Instagram, WhatsApp and Telegram — so as to cause them to show up increasingly practical.
Once infected, the smartphone would be related directly to
Hamas’s servers and the terror team ought to prompt its digital camera to take
pictures, download archives from the gadget and see the soldiers’ contacts and
GPS data.At that point, the Hamas operatives would give up communicating
with the soldiers.
Resh said the IDF used a new approach to take down Hamas’s
servers and thwart the catfishing effort, but refused to tricky on it.She
said new warnings were being dispatched out to soldiers, telling them now not
to discuss to humans they don’t be aware of on social media, to avoid sharing
classified information and to immediately alert an operational safety officer
or their commander if their telephones commence behaving strangely.
The IDF said the pix used by using Hamas had been edited and
altered in order to make it difficult to find their original source. The navy
said it did now not comprehend to whom the photographs used by Hamas without a
doubt belonged. As a result, the IDF stated it did not contact these girls
before using their images in its media campaign about the Hamas cyber operation
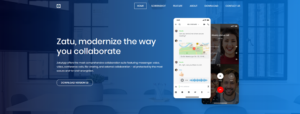
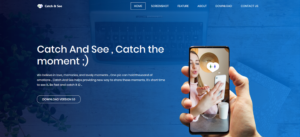
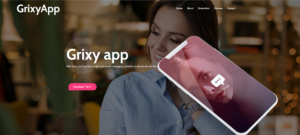
The 2020 iteration combines a little of both 2017 and 2018 efforts. This time around three new applications were created by Hamas, GirxyApp, ZatuApp and Catch&See. The backstopping of the applications included a website.